Introducing: The echo-trivy integration
.png)
Scan clean with the echo-Trivy integration
Scanners play an essential role in container security, providing clear visibility into the vulnerabilities that exist in your application software.
But what happens when you use open source base images? Well, your scanners are inherently loud – alerting you to hundreds, if not thousands, of CVEs in a single scan, and flagging everything it finds, regardless of whether it’s relevant, fixable, or even reachable by your application. The result? Tons of friction. Engineers spend hours triaging vulnerabilities they didn’t introduce, security teams struggle to get certain risks prioritized and prove what's actually been mitigated. And teams are left debating red flags rather than shipping software.
Enter: the echo-Trivy integration. Now, when you build with echo’s CVE-free base images, Trivy scans will show what’s true: a clean foundation with zero known CVEs. No configuration required or workflow changes – just instant visibility into your strong security posture.
With echo and Trivy working together, your base images don’t just start clean – they stay clean, and now your scanners can prove it.
How echo eliminates CVEs at the source
The key to clean scans isn’t post-scan filtering or exception lists – it’s eliminating vulnerabilities before they ever appear. echo tackles this at the source by rebuilding open source base images from scratch. Our platform uses AI agents to analyze each upstream image and build it with only the essential components needed for functionality. The result is a minimal, hardened version of the image that mirrors, or echoes, the original behavior with a dramatically smaller attack surface – ensuring it scans clean without breaking your app.
And we don’t stop there. echo images are continuously monitored and patched to ensure they stay CVE-free over time. When a new vulnerability is disclosed, our system automatically rebuilds affected images and ships the updated versions to ensure your scans don’t get noisy.
Why the Trivy integration was a must
Trivy was an essential integration for echo – not just because it’s popular, but because it’s trusted. With over 100 million downloads a year and millions of developers relying on it daily, Trivy has become the standard for vulnerability scanning across containers, Kubernetes, cloud infrastructure, and more. It’s fast, flexible, open source, and already embedded into CI/CD pipelines and dev workflows around the world.
And when a base image includes a CVE, Trivy is the tool that surfaces it – in PR checks, in pipelines, in production scans. So if we’re going to help teams eliminate noise and reduce unnecessary triage, it’s essential for Trivy to be able to recognize that improvement.
By integrating directly with Trivy, echo gives teams a seamless way to verify that their images are clean – using the scanner they already trust. No need for new workflows, dashboards, or policy rewrites. The integration is seamless for users and guarantees cleaner results immediately.
Fun fact: Trivy’s vulnerability database is updated every six hours to keep up with the latest advisories from Linux distributions and other sources. That means when you scan an image, you’re getting near real-time visibility into newly disclosed CVEs.
How does the Trivy integration work in practice?
To understand how the integration works, we first need to examine the scanning process itself, which consists of three stages: creating the vulnerability database (DB), generating SBOMs, and detecting vulnerabilities. Each stage is essential for producing a complete and accurate scan.
1. Vulnerability database creation
Trivy stores CVE data in a local vulnerability database (DB), which is downloaded during the scan to enable matching the image’s SBOM to known vulnerabilities. The DB is built from public advisories for container operating systems. For example, Debian’s advisory is published via a JSON file whenever its security tracker detects an update. With the new Trivy integration, echo's advisory is now included in this database, and our security updates are published daily to Trivy’s DB.
2. SBOM generation
To generate the SBOM, Trivy analyzes the image, scans each file, extracts relevant information, and aggregates it into a single SBOM manifest. It pulls information from local OS files that describe the image, including installed packages, license data, the image distro, package dependency tree, go binaries, and more. Because echo is fully integrated with Trivy, it can easily detect when the image is based on echo and accurately locate all installed packages and binaries.
3. Vulnerability detection
Lastly, the vulnerability detection stage leverages the SBOM and matches it against the vulnerability database to generate a complete report of the image’s packages and any associated vulnerabilities. Based on the detected operating system and the analyzed packages, Trivy cross-references the data with the vulnerability database to identify which CVEs are present in the image. Our integration ensures that echo’s security patches are incorporated into the scan results as quickly as possible.
What this integration means for your team
Trivy scan with echo image:
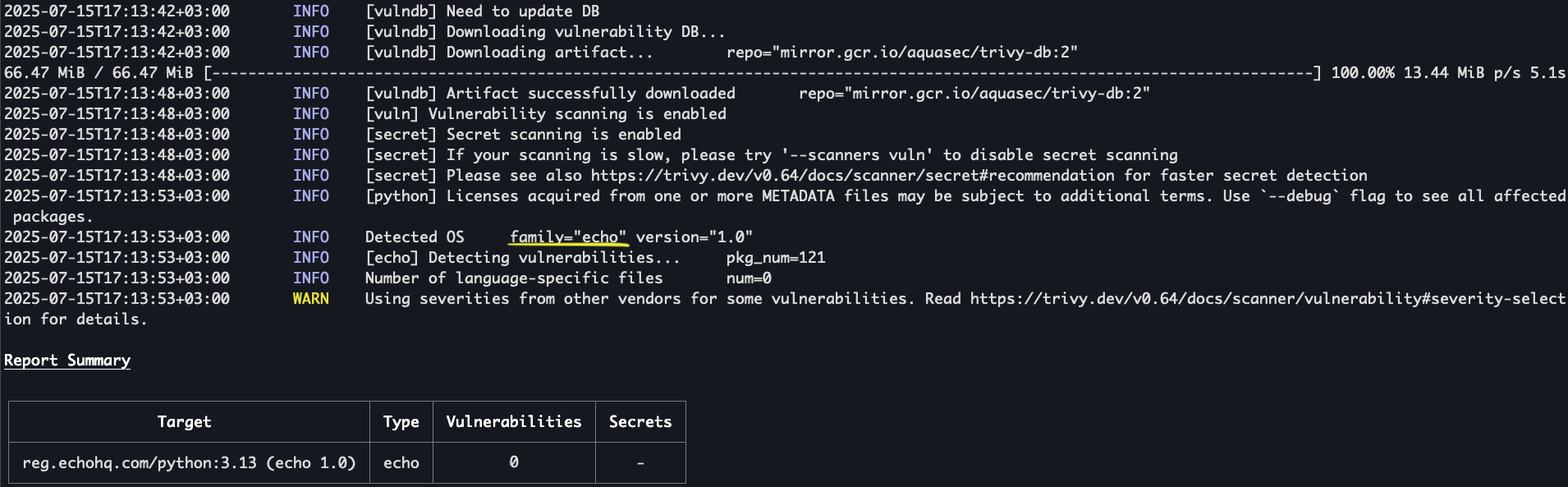
We recognize that the smoother the experience, the greater the benefits for our customers and the higher the likelihood of real adoption. That’s why, whether you use Trivy, another open source scanner, and/or a commercial CNAPP, echo is fully integrated – to avoid disruptive changes to your tooling and workflows.
With these seamless integrations, your images will scan clean, your reports will reflect a strong security posture, and your teams will spend less time arguing over false positives and more time driving business value.
.png)
.png)
.avif)