echo partners with Orca to deliver CVE-free scans in your CNAPP
.jpg)
If you’ve ever built with open source container base images, you know that they’re typically filled with inherited vulnerabilities that flood your CNAPP dashboards, create massive cross-functional friction, and slow down remediation – even if they’re not relevant to the app.
That’s why we’re thrilled to announce a new integration between Orca and echo, which quiets that noise and makes container security more effective across the board. With echo’s secure-by-design base images that are free of known CVEs, and Orca’s deep, contextual visibility into risk across their cloud environments, you can now see the impact of echo’s clean container foundations directly inside Orca’s CNAPP – giving your security teams a faster, clearer way to understand what needs attention and what’s already handled. With the echo-Orca integration, enjoy fewer false positives, faster triage, and greater confidence that your infrastructure is secure.
echo removes risk at the source
When it comes to open source container base images, CVEs come baked into the operating system, runtime, and libraries, and they show up across every container built on top. That’s why echo’s AI agents target this at the source – analyzing commonly used open source base images and rebuilding them from scratch to be CVE-free, without compromising on functionality or compatibility. These base images contain zero known CVEs and are continuously maintained to stay that way. The images are seamless to swap with zero workflow disruptions, alleviating a passive burden from security, engineers, and DevOps teams.
A more focused workflow
Once echo’s clean base image is deployed, Orca picks it up immediately at runtime, showing a dramatically reduced vulnerability surface, with no base-layer CVEs. This ensures that what you do wind up seeing in Orca reflects true risk: application-level issues that are actually worth fixing. With echo’s suppression of inherited risk and Orca’s correlation of real-world context, security teams can:
- Instantly confirm when base image CVEs have been eliminated
- Prioritize vulnerabilities that truly impact the business
- Cut down on duplicate work between security and engineering teams
- See the full picture – from build to runtime – in one unified view
Built for your existing stack
Both echo and Orca are designed to work with your existing workflows and tooling. echo’s base images are drop-in replacements that don’t require you to change your CI/CD setup or your operating system.
Orca processes echo images the same way it does open-source base images, enriching them with runtime context, reachability analysis, and prioritization based on actual exposure.
Setup takes minutes, the payoff is immediate, and the impact across teams is massive.
Orca scan with an open-source image:
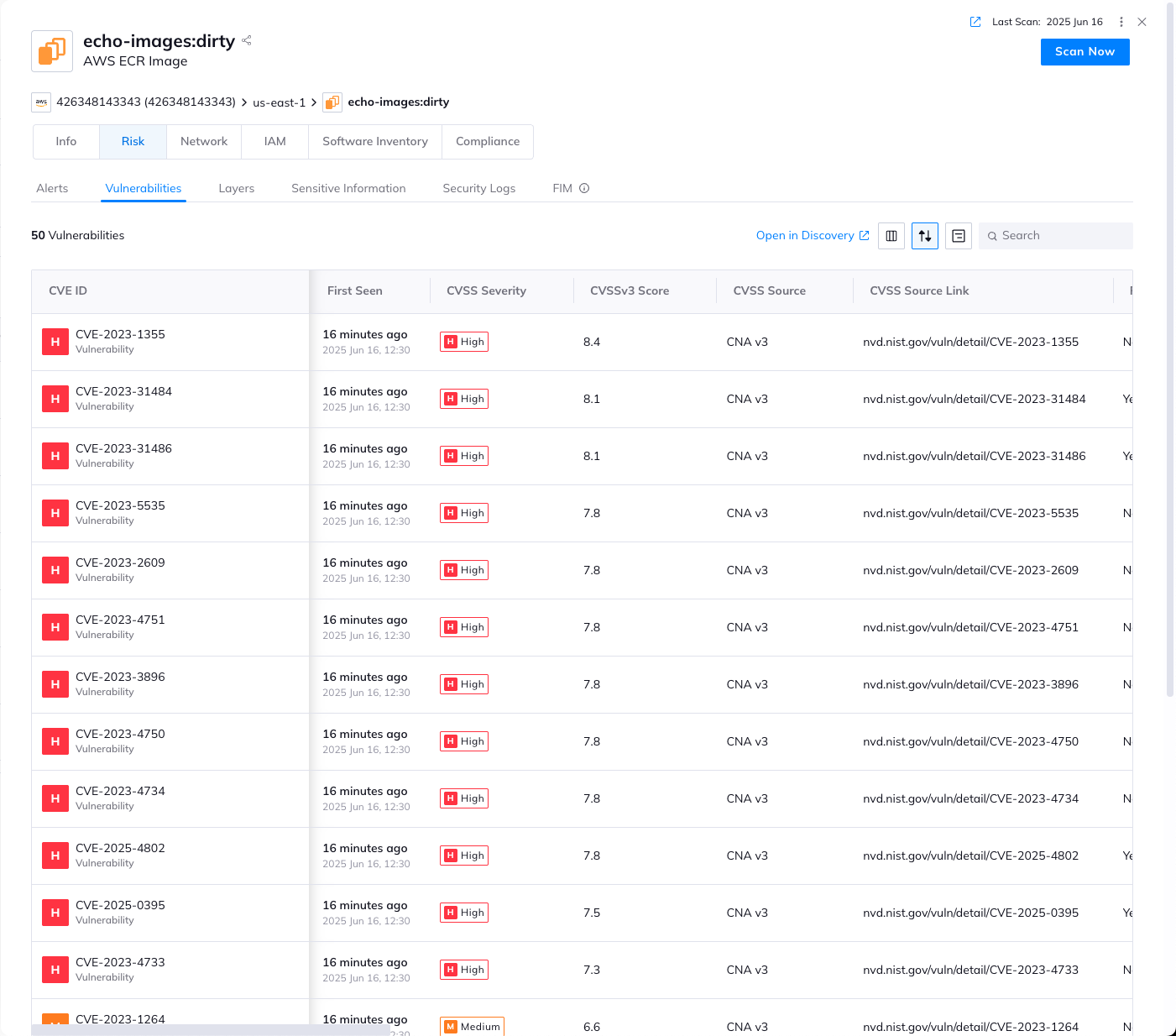
Orca scan with an echo image:
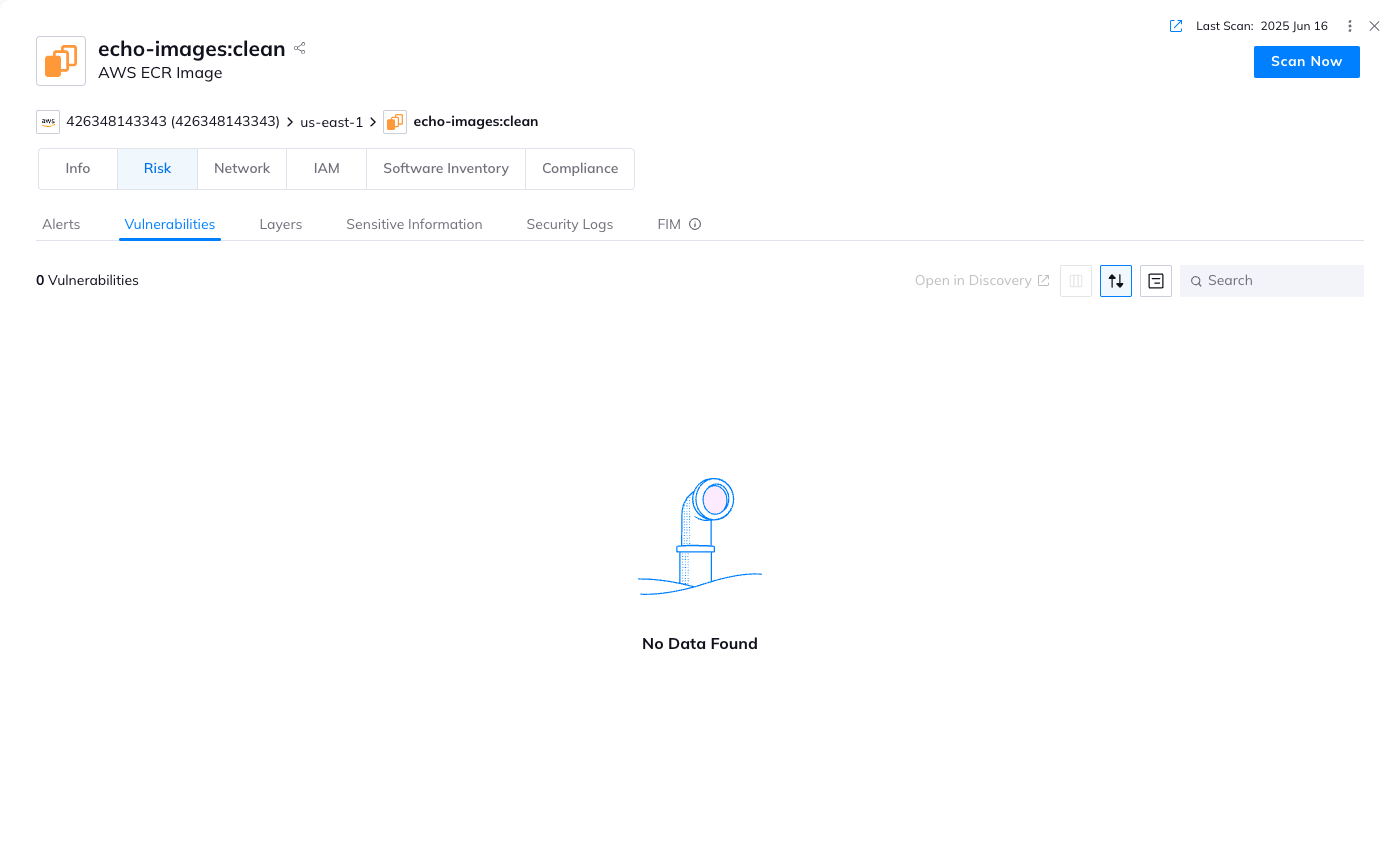
Available now
The Orca-echo integration is live and available to all joint customers. It’s a simple but powerful way to eliminate vulnerability noise at the source – and validate that work in runtime.

.png)
.avif)